iptables forward chain 2020 (4)
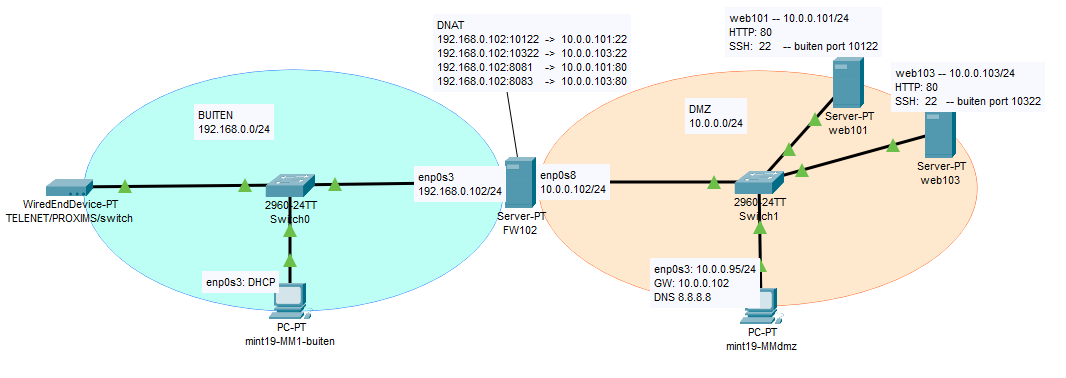
packettracer-file: fwv004-dnat-router
- config voor forwarding ssh naar web 101 only
#! /bin/bash # # iptables-script # bvdb ( 29/04/2020 ) (v005) ##################################################### # # here follows the script ....1 # v = verbose, X = flush tables, F = delete non standard chains # general iptables -vX iptables -vF # nat and masquerading -t refers to table iptables -vt nat -F iptables -vt nat -X # mangling TCP header iptables -vt mangle -F iptables -vt mangle -X # reset policies -P refers to policies # iptables -vP INPUT ACCEPT ## we are going to close the INPUT CHAIN iptables -vP OUTPUT ACCEPT #iptables -vP FORWARD ACCEPT # turn off routing # echo 0 > /proc/sys/net/ipv4/ip_forward ###################### iptables is nu cleared #### # turn on routing echo 1 > /proc/sys/net/ipv4/ip_forward ###### Dit is heel belangrijk in je script -- ###### dan zie je wat je aan het doen bent: # ##>> my network interfaces: enp0s3 = 192.168.0.102/24 >> buiten ##>> my network interfaces: enp0s8 = 10.0.0.102/24 >> DMZ (binnen) ### implement NAT routing # ## NAT routing - enp0s3 is buiten en een unprotected network # het ip address aan de buitenkant van onze firewall is 192.168.0.102 (outside address) # iptables -vt nat -A POSTROUTING -o enp0s3 -j SNAT --to 192.168.0.102 ### implement INPUT filtering ## INPUT chain lo + ports 10022 iptables -vP INPUT DROP iptables -vA INPUT -i lo -j ACCEPT iptables -vA INPUT -p TCP --dport 10022 -j ACCEPT iptables -vA INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT #### Destination NAT - iptables -vP FORWARD DROP ## destination forward ports iptables -vA FORWARD -p TCP --dport 22 -j ACCEPT iptables -vA FORWARD -p TCP --dport 10122 -j ACCEPT iptables -vA FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT ## port 10122 >> web101:22 (ssh) iptables -vt nat -A PREROUTING -p TCP --dport 10122 -j DNAT --to 10.0.0.101:22 ###################### iptables is nu ingesteld #### ### PRINT iptables configuration ### # echo ">>>>> iptables -n -L" iptables -n -L echo "--------------" echo ">>>>> iptables -S" iptables -S echo "--------------" echo ">>>>> iptables -t nat -L" iptables -t nat -L echo "--------------" echo ">>>>> iptables -t mangle -L" iptables -t mangle -L echo "--------------" echo "routing set: " `cat /proc/sys/net/ipv4/ip_forward` echo "==============" - config voor forwarding ssh/http naar web101 en web102
#! /bin/bash # # iptables-script # bvdb ( 29/04/2020 ) (v005) ##################################################### # # here follows the script ....1 # v = verbose, X = flush tables, F = delete non standard chains # general iptables -vX iptables -vF # nat and masquerading -t refers to table iptables -vt nat -F iptables -vt nat -X # mangling TCP header iptables -vt mangle -F iptables -vt mangle -X # reset policies -P refers to policies # iptables -vP INPUT ACCEPT ## we are going to close the INPUT CHAIN iptables -vP OUTPUT ACCEPT #iptables -vP FORWARD ACCEPT # turn off routing # echo 0 > /proc/sys/net/ipv4/ip_forward ###################### iptables is nu cleared #### # turn on routing echo 1 > /proc/sys/net/ipv4/ip_forward ###### Dit is heel belangrijk in je script -- ###### dan zie je wat je aan het doen bent: # ##>> my network interfaces: enp0s3 = 192.168.0.102/24 >> buiten ##>> my network interfaces: enp0s8 = 10.0.0.102/24 >> DMZ (binnen) ### implement NAT routing # ## NAT routing - enp0s3 is buiten en een unprotected network # het ip address aan de buitenkant van onze firewall is 192.168.0.102 (outside address) # iptables -vt nat -A POSTROUTING -o enp0s3 -j SNAT --to 192.168.0.102 ### implement INPUT filtering ## INPUT chain lo + ports 10022 iptables -vP INPUT DROP iptables -vA INPUT -i lo -j ACCEPT iptables -vA INPUT -p TCP --dport 10022 -j ACCEPT iptables -vA INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT #### Destination NAT - iptables -vP FORWARD DROP ## destination forward ports iptables -vA FORWARD -p TCP --dport 22 -j ACCEPT iptables -vA FORWARD -p TCP --dport 80 -j ACCEPT iptables -vA FORWARD -p TCP --dport 10122 -j ACCEPT iptables -vA FORWARD -p TCP --dport 10322 -j ACCEPT iptables -vA FORWARD -p TCP --dport 8081 -j ACCEPT iptables -vA FORWARD -p TCP --dport 8083 -j ACCEPT iptables -vA FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT ## port 10122 >> web101:22 (ssh) iptables -vt nat -A PREROUTING -p TCP --dport 10122 -j DNAT --to 10.0.0.101:22 ## port 10322 >> web103:22 (ssh) iptables -vt nat -A PREROUTING -p TCP --dport 10322 -j DNAT --to 10.0.0.103:22 ## port 8081 >> web101:80 (http) iptables -vt nat -A PREROUTING -p TCP --dport 8081 -j DNAT --to 10.0.0.101:80 ## port 8083 >> web103:80 (http) iptables -vt nat -A PREROUTING -p TCP --dport 8083 -j DNAT --to 10.0.0.103:80 ###################### iptables is nu ingesteld #### ### PRINT iptables configuration ### # echo ">>>>> iptables -n -L" iptables -n -L echo "--------------" echo ">>>>> iptables -S" iptables -S echo "--------------" echo ">>>>> iptables -t nat -L" iptables -t nat -L echo "--------------" echo ">>>>> iptables -t mangle -L" iptables -t mangle -L echo "--------------" echo "routing set: " `cat /proc/sys/net/ipv4/ip_forward`